Information Security
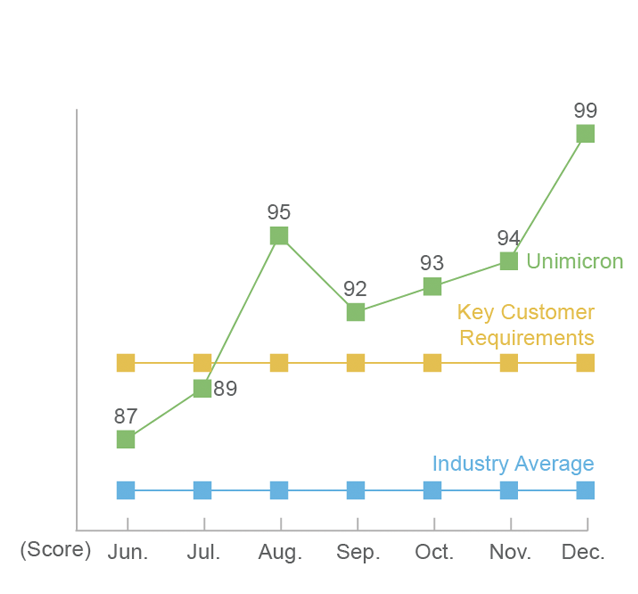
Protecting customers' intellectual property rights and business information is the focus of our business and business ethics management. Through a comprehensive "Information Security Policy" and the control of ISO 27001 Information Security Management System, Unimicron's main focus of information security in 2022 is supply chain information security management. As a key partner in our customers' upstream supply chain, Unimicron is committed to enhancing customer confidence and achieving better than industry average and key customer requirements through various third-party information security audit platforms, proving Unimicron's information security maturity is better than the standard.
Information Security Maturity Assessment for the Second Half of 2022
Information Security Goals
In order to maintain the confidentiality, integrity and availability of the Company’s information assets, and to protect the privacy of customers and personal data, Unimicron has formulated an information security policy and hopes to achieve the following goals through the joint efforts of all employees in the Company:
Confidentiality:Ensure that only authorized personnel can obtain information and avoid information leakage.
Integrity: Ensure that information is not subject to unauthorized tampering and the correctness of information processing methods.
Availability: Ensure that authorized users can obtain information and use related assets when needed.
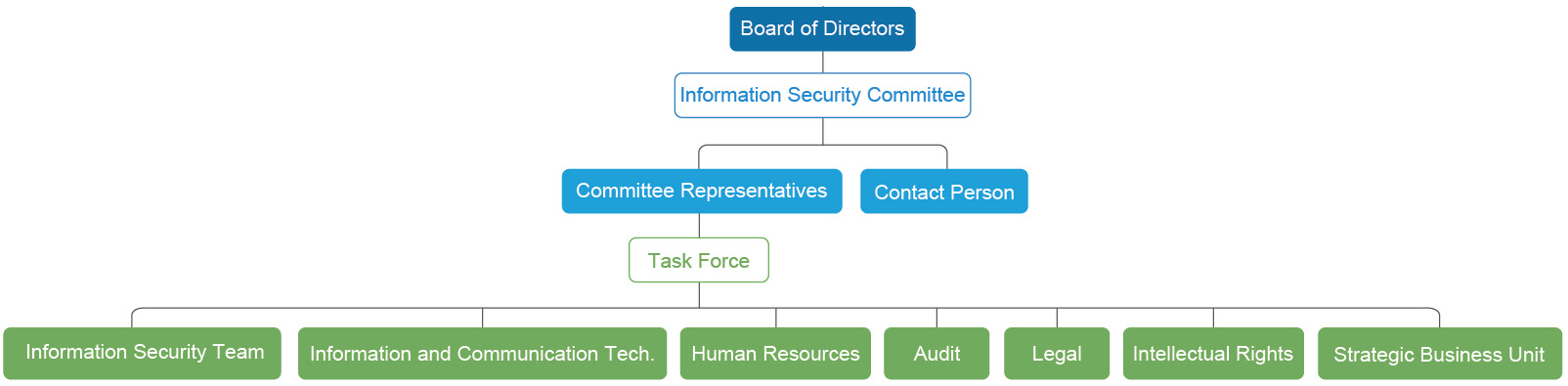
Information Security Committee
Unimicron has set up an Information Security Committee to manage the information protection mechanism at the corporate level. In 2022, the Company established a Chief Information Security Officer (CISO) and a dedicated information security unit to lead biweekly information security meetings and improve operations through PDCA rolling reviews, including mechanisms such as internal information security advocacy and drills, asset inventory and classification, data access control, information security alerts, etc., regularly providing information security reports to the Chairperson of the Board of Directors and senior executives of our business divisions and obtaining international information security certification, to reduce information security risks and protect customer privacy.
The Role & Responsibility of Information Security SIG
| Information Security Team |
• Host security meetings
• Formulating security policies and strategies |
| Information and Communication Tech. |
• Systems and technical management assessment
• Security system maintenance and permission adjustment |
| Human Resources |
• Training scheduling and announcement
• Staff regulations and reward/punishment process |
| Audit |
• Effectiveness assessments of security policies
• Security incidents escalation and following |
| Legal |
• Security related laws and regulations following
• Legal interpretation and consulting |
| Intellectual Rights |
• Trade secret and patents asset review and value definition assistance
• Trade secret and patents system maintenance |
| Strategic Business Unit |
• Promoting security policies to departments and keep following
• Submit feedback from departments and be bridges between business units and committee
• Respond to security incidents in business units |
Information Security Management Plan
To protect customers' intellectual property rights and confidential corporate documents, in addition to a comprehensive information security policy and annual ISO/IEC 27001 Information Security Management System certification, Unimicron develops specific management related to the six major aspects of Risk Assessment, Terminal Computer Management, Computer Room Management, Anti-virus and Anti-hacking Management, System and Network Security Management, and Training to properly maintain customer data and information security.
During the pandemic period, the email application was promoted to cloud services, and virtualized desktops were used to support the operational resilience of remote working during the pandemic period. At the same time, a web application firewall was built to actively protect the information security vulnerabilities of the Group's external websites. In response to the full termination of support for Microsoft's IE browser, corrections of internal system compatibility were made, and Managed Detection and Response (MDR) service was also provided to strengthen Unimicron's overall information security protection and mitigate risks.
Risk Assessment
Measures:We review risks and management measures through ISO 27001 Information Security Management System and company-wide bi-weekly Information Security Committee meetings, and submit bi-monthly reports.
Achievements:Build a web application firewall, define and strengthen machine risks in the factory area, correct compatibility of various systems in response to the elimination of IE platform, promote email encryption in the upstream supply chain, strengthen the identification of watermarks of smart business machines, gradually replace client operations system, etc.
Training
Through physical and digital E-based courses, regularly conduct 3 training and verification of "information security," "trade secret protection" and "patent and copyright protection" to employees, to establish employees' awareness of sensitive information protection, and implement trade secrets inventory and classification management every year to protect Company and customer data.
System and Network Security Management
Completed 12 vulnerability scans and bug fixes according to Information Security Control Guidelines for Listed and OTC Companies and customer requirements.
Terminal Computer Management
Utilize the Managed Detection and Response (MDR) service to establish an advanced continuous threat detection mechanism to quickly detect abnormal behaviors of the system’s information security.
Computer Room Management
Use the following three sets of systems to support each other to construct a secure physical computer room environment and to protect the system and customer data security:
Central Access Control System: Control the entrance and exit of the computer room, allowing only authorized employees to access, while retaining the entry and exit records and integrating face recognition system gradually.
CCTV System: Have 24-hour full-area video monitoring of the computer room, and through the sensing mechanism, automatically send out an alarm when an abnormal intrusion occurs.
Environmental Control System: Monitor the environment (temperature, humidity, power) of the computer room 24 hours a day.
Anti-Virus and Anti-hacking Management
Strengthen the Machine Protection: Introduce the machine virus-free certificate management mechanism. The firm supplying the machine shall submit a virus-free certificate, and the machine can only be connected to the network after it is checked by Unimicron to be virus-free. Regular anti-virus audits shall be conducted on the machines.
Network Firewalls and Hacker Intrusion Detection and Defense Systems: To detect, block and alert about external threats and with the help of external information security organizations, provide Security Operation Center (SOC) services, 24-hour round-the-clock information security incident analysis mechanism.
2022 Information Security Management Results
Supply Chain Information Security Management
Key suppliers are required to set up email Sender Policy Framework (SPF) and Transport Layer Security (TLS) to ensure secure data exchange. We have also strengthened the depth of organizational defense through various third-party information security audit platforms, and the rating of the Group exceeds industry standards and key customer requirements on each platform.
Security Operation Center (SOC)
Complete the establishment of the Security Operation Center (SOC) service in Taiwan for rapid response to information security incidents by 2022.
Definition of Factory and Machine Risk and Strengthening
According to the protection and resilience, the machines are classified into four risk levels, such as A, B, C, and D in Taiwan. 360 high-risk (A class) machines have been mitigated and will be continuously improved in 2023.
Internal Information Security Advocacy and Drill
We hold regular information security advocacy and testing for employees, in 2022, we issued 4 announcements, held 9 unannounced social attack drills (phishing email), and conduct a companywide e-Learning information security course in the fourth quarter of each year to deepen employees' information security awareness through experience.
| Email Drill |
Test Subjects |
Result |
Enhancement Measures |
| First Test |
Employees with Email accounts |
Open malicious link and enter account password: 0.6% (2.2% in 2021 / 3.1% in 2020) |
For employees who failed the test, Unimicron has completed the second propaganda and arranged a test |
| Retest |
Employees who failed the first test (217 employees failed the test) |
Open the malicious link and enter account password: 4 employees failed the test |
Individual training by the supervisor |
2022 Information Security Training Course
Note 1: The employees on board since April 1, 2022, who have not completed the training will be included in the training list for the following year.
Note 2: 2 employees who have not completed training, 1 employee was on long-term sick leave, and 1 employee was on maternity leave.
Note 3: The training starts from July 1 to Sep. 16, 2022, employees who should be trained are Taiwanese and Taiwanese employees (including DL) stationed in Mainland China at level 5 (or above) who have arrived at least three months before March 31, 2022.
Important Information Security Project
In response to the increasing complexity of external attacks, Unimicron has adopted a defense-in-depth concept for information security protection by adopting protection mechanisms of deploying firewalls, mail filtering, endpoint security protection, Multi-Factor Authentication, and other protection mechanisms to protect information assets. We also use an external third-party information security testing platform as an objective basis to measure the maturity of information security. In 2022, we introduced Security Operation Center (SOC) mechanism to enhance the visibility of each information link and accelerate the response speed to information security incidents and adjusted the information security framework through regular audits to meet the requirements of continuous operations and regulatory authorities.
Information Security Incident Notification Process
Occurrence of Incident
Report immediately in accordance with "Unimicron’s Information Security Incident Notification Management Procedures".
Reporting
• The unit head reports to the Information Security Officer.
• The Information Security Officer classifies incidents according to internal Information Security regulations, whether the case is a major anomaly, whether the case is a breach of confidentiality, and whether the case involves a first-level supervisor.
Handing of Leakages
It shall be reported to the supervisor at that level and the responsible unit. If it is a major event, it must be reported to the first-level supervisor and the president of the business division, Chief Information Security Officer and the Executive President. If it is a major abnormality and suspected leak event, it shall be reported to the Human Resources Department and the Audit Office.
Handling of the Information Security Incident
It shall be handled by the Legal / Human Resources Department under law or regulations.
Case Closure
If it is an information security incident of level 3 or higher, the "Information Anomaly Incident Report" must be filled out and submitted to the Information Security Officer or higher.
2022 Information Security Enhancement Measures
In 2022, in order to enhance the company's overall information security capabilities, the following management plans have been strengthened and completed.:
• Flow Control: Strengthen internal and external cross-plant firewall and abnormal flow detection and analysis capabilities, endpoint computer data output record check and analysis.
• Account Control: Strengthen multi-factor authentication and authorization control of bastion hosts.
• Backup Optimization: Data backup and instant recovery structure improvement.
• Governance Policy: Enhancing vulnerability scanning, 24H service, and Security Operation Center (SOC), USB management, hand-held mobile camera device management, information classification security system, printing control, employee information security training and phishing drills, etc.
• Investing Resources: Set up the Chief Information Security Officer (CISO) and a dedicated information security organization, and join the information security sharing organization Taiwan Computer Emergency Response Team / Coordination Center (TWCERT).
Information Security Incident